Explain Different Application of Ip Security
Establishing extranet and intranet connectivity with partners. These security standards might be applied to the network the operating system application software even programs written by the person who administers your system.
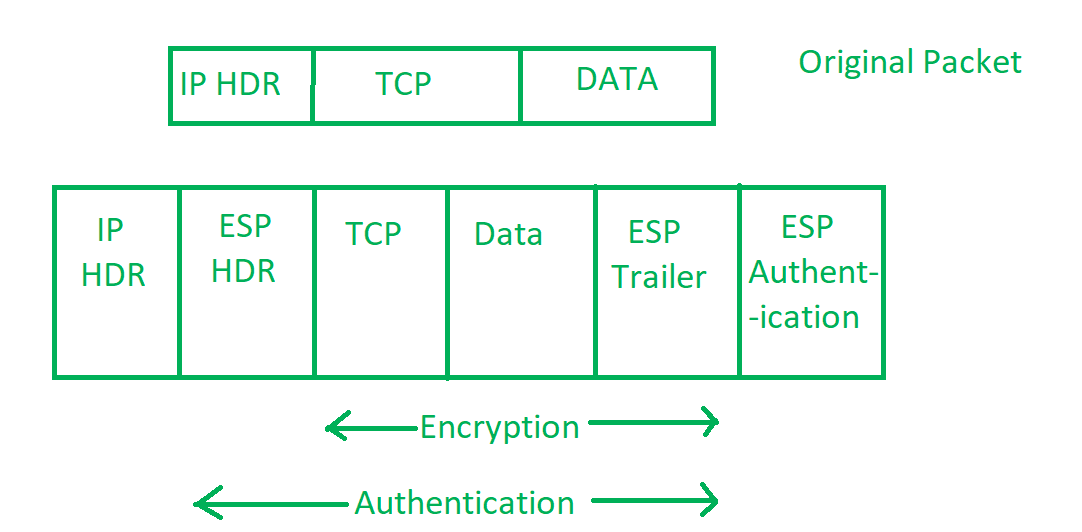
Ip Security Ipsec Geeksforgeeks
Up to 20 cash back An IP address is a unique address that identifies a device on the internet or a local network.
. The Internet was not created with security in mind. Making the distinction between a firewall and other security solutions can. The Imperva applicati on security solution includes.
IP stands for Internet Protocol which is the set of rules governing the format of data sent via the internet or local network. The IPsec suite also includes Internet Key Exchange IKE which is used to generate shared security keys to establish a security. DoS eavesdropping Spam over Internet Telephony SPIT VoIP network infrastructure the VoIP application itself and IP vishing etc.
This section describes the security features provided with Transmission Control ProtocolInternet Protocol TCPIP both in standard mode and as a secure system and discusses some security. Authentication Header AH and Encapsulating Security Payload ESP. Finding the right network security tools to secure your sensitive data can be a significant challenge for any organization.
Answer 1 of 3. VoIP network faces a lot of vulnerabilities are subjected to different attacks such as Denial of Service that can be related to one of the following three categories. In essence IP addresses are the identifier that allows information to be sent between devices on a network.
Different types of application security features include authentication authorization encryption logging and application security testing. Network layer security controls have been used frequently for securing communications particularly over shared networks such as the Internet because they can provide protection for many applications at once without modifying them. It involves frame rate conversion motion detection reduction of noise and colour space conversion etc.
In the earlier chapters we discussed that many real-time security protocols. Secure remote access over the Internet. Authentication procedures ensure that a.
When software developers build procedures into an application to ensure that only authorized users gain access to it. Developers can also code applications to reduce security vulnerabilities. This layer is the abstraction layer which handles the sharing protocols over the computer network with OSI and TCPIP model.
Network Security Network Layer. IPsec originally defined two protocols for securing IP packets. Communications can be altered examined and exploited.
The server component is a service provider that controls commonly shared resources pertaining to a particular application on the network. The former provides data integrity and anti-replay services and the latter encrypts and authenticates data. Choosing a firewall may seem like a simple task but companies can get overwhelmed by the different firewall types and options.
Applications of IP Security Secure branch office connectivity over the Internet. To secure applications and networks across the OSI stack Imperva provides multi-layered protection to make sure websites and applications are available easily accessible and safe. Application layer is the last and 7th layer of the OSI model.
Information as a valuable asset of an. Enhancing electronic commerce security. This blog was written by a third party author.
DDoS Protectionmaintain uptime in all situations. In internet protocol suite the application layer contains communication protocols and interface methods which used for the process to process communication. A collection of frames or pictures are arranged in such a way that it makes the fast movement of pictures.
It is also one of the applications of digital image processing. TCIP applications operate at the application or process layer of the TCPIP hierarchy as discussed in the preceding sectionsTCPIP protocol splits an application into server and client components. There is a growing need to protect private information crossing the public networks that make up the Internet infrastructure.
Next Topic Concept of Dimensions. Prevent any type of DDoS attack of any size from preventing access to your.
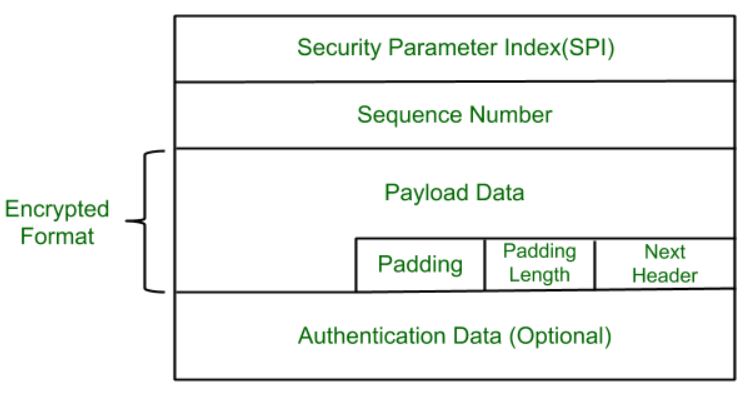
Ipsec Architecture Geeksforgeeks
No comments for "Explain Different Application of Ip Security"
Post a Comment